how do *i* know that this is actually showing me data at all, and not some unsupported PIDs that are just generic defaults?
One benefit of using a smartphone based app like Torque Pro or OBDFusion is for the most part you have more control over operations than you would with a partshouse type scanner. With those you have no idea what is being done in the background. Yes they pull up data but from where and how?
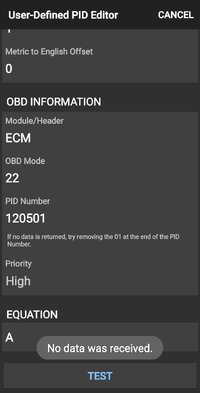
In a phone app like OBDFusion if interested you can go to settings, user defined PIDs, then scroll down to one of the misfire PID entries. Tap on the entry and select "edit". Here you can view the specifics of the PID.
Under the heading "OBD INFORMATION" you will see a 'module/header', an 'OBD Mode' and a PID number as well as an 'equation'.
The Module/Header is header of the message frame to be sent. This determines which in vehicle microcontroller the message is sent to. In your case it may just read "ECM". Just to make it easier for the user, in the background the OBDFusion app will substitute the actual hexadecimal information corresponding to your ECM for your particular network protocol. This is likely to be "7E0" for a CANBUS network. For an SAE J1850 VPW protocol like the class 2 serial data network the ECM/PCM address is usually "10" for a GM product.
The OBD Mode means what service are you requesting from that microcontroller. Our ECM/PCM/whatevers offer a variey of services (previously termed modes). Service/Mode 22 is defined as 'request diagnostic data by parameter ID'. A message requesting this service is going to call that specific service from the module, in this case your ECM.
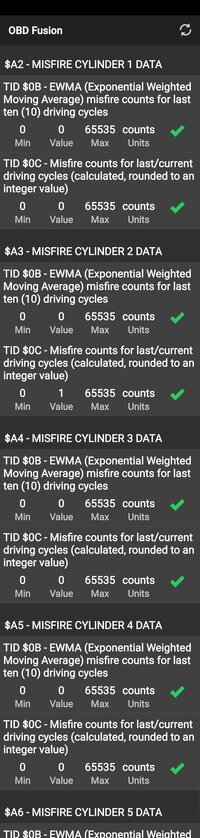
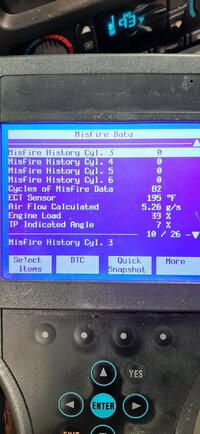
Service/mode 22 accepts a 2 byte parameter ID as the first argument. That is the PID number. In the case of current misfire counts for cyclinder 5 the parameter ID is 11EA (hexadecimal). The service/mode will return the byte(s) currently stored for that parameter. It will not substitute defaults or anything of that sort. Service 22 is not coded to do anything like that.
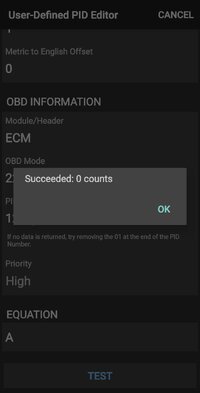
OBDFusion takes the returned value and uses that in the "equation" to derive the value it then reports to the display. The data bytes returned by service/mode 22 are converted from hexadecimal to decimal and then 'tokenized' by OBDFusion, first data byte value is represented by "A", second data byte value is "B" and so on.
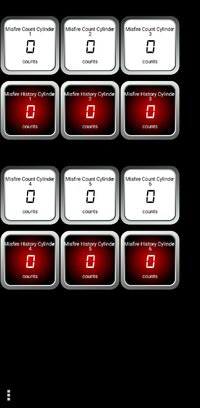
In the case of misfires the value is a simple 'count' which does not require an elaborate equation. The current count is a single byte value, the history count is a 2 byte value.